Searching with the UI
PolySwarm supports Hash Searching, Metadata Searching and IOC Searching. This section will cover how to use these functions in the UI.
Hash Searching
Searching by Hash allows you to find Artifacts that match a given hash. We support searching by MD5, SHA1, and SHA256.
Hashes can be entered into the multi-use text box below the “Select file” button on the Scan page. They can also be entered into the text box on the Search page’s Hash Searching tab.
On the Hash Searching tab, clicking the "Search Multiple" toggle above the search box will allow the user to enter a list of hashes to be searched. When multiple hashes are searched, the hash results will display in the same order as the list of hashes provided.
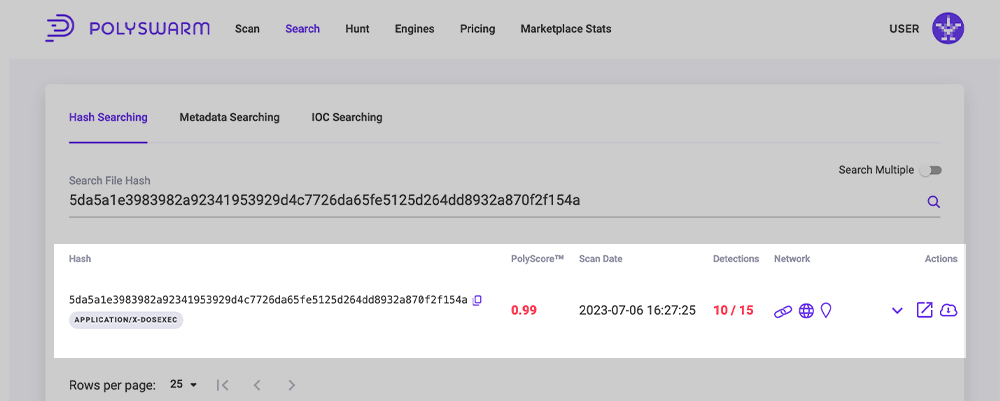
Hash Search Results
Hash search results are listed on the Search -> Hash Searching tab. The below covers what is displayed in the table once you search a hash.
| Button | What is it for? |
|---|---|
| Hash | SHA256 hash of the Artifact with the file MIME type. |
| PolyScore | Threat scoring algorithm that provides the probability that a given file contains Malware. One being the highest number and will contain Malware, Zero being the least chance. |
| Scan Date | Date that the Artifact was last scanned by the Engines. |
| Detections | Detections column shows the engine detection results, which can be one of Four items:
|
| Network | Icons to highlight the available network data via the metadata, if the icon is colored, that type of network data is available:
|
| Actions | The Actions column has an icon that allows you to get more information about the artifact:
|
Metadata Searching
Searching by Metadata allows you to find Artifacts that have a variety of attributes or content. We support queries using the ElasticSearch Query String syntax.
Metadata searches can be entered into the search bubble on the landing page. They can also be entered into the Search Metadata box on the Search -> Metadata Searching tab. To understand how to build out a Metadata query see the How-To Guide.
The Search Metadata box records your most recent queries and will suggest them as you type future queries. You can remove queries from the list of recent queries by clicking the "X" icon at the far right side of the query entry.
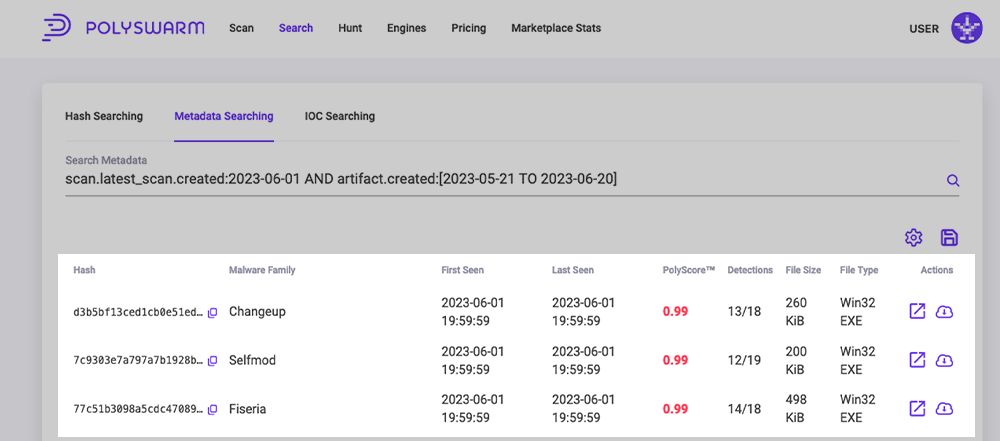
Metadata Search Results
When a Metadata Search Query is run, the search results will be listed in a table below the Search Metadata box. The below covers what is displayed in the table once you search a hash.
| Button | What is it for? |
|---|---|
| Hash | SHA256 hash of the Artifact with the file MIME type. |
| Malware Family | The Malware Family shows the PolyUnite malware family. |
| First Seen | Date the Artifact was first seen in PolySwarm. |
| Last Seen | Date the Artifact was last seen in PolySwarm. |
| PolyScore | Threat scoring algorithm that provides the probability that a given file contains Malware. One being the highest number and will contain Malware, Zero being the least chance. |
| Detections | Detections column shows M/T (Malicious/Total) where Malicious is the number of engines that found the artifact to be malicious and Total is the total number of engines that analyzed the artifact. |
| File Size | Size of the Artifact File. |
| File Type | File Extension Type of the Artifact. |
| Actions | The Actions column has icon that allow you to get more information about the artifact:
|
At the top right of the table are buttons that allow you to change how the results are displayed as well as to save the results.
- Gear: Drop down that allows you to check/un-check column names to hide/unhide them. Plus, you can drag/drop column names in the drop down to re-order them.
- Floppy Disk: Allows you to save the currently displayed results as a CSV file. Only the data in the visible columns of the current page of results are saved.
Notes:
- The results in the table are sorted with the most recently submitted file first.
- The results are paginated, defaulting to 25 per page.
- You can edit the page size using the dropdown menu in the lower left of the table.
- Next to that are buttons to go to first, previous, and next page of the results.
Be aware that each page of metadata search results that is viewed is counted as one use of your Metadata Search quota. Changing the "Rows per page" will reload the page, and also uses one use of your Metadata Search quota.
IOC Searching
IOC Searching can be split into two types of Searches, these are:
- Searching for Associated IOCs related to a Hash: This returns IOCs that were observed by our sandbox during analysis. These IP's and Domains are classified as C2 or malicious.
- Searching for Associated Hashes related to an IP, URL, imphash or MITRE TTP: This returns file hashes that were seen communicating with the specified IPs or domains in our sandbox — regardless of whether the communication was malicious or not.
Access the IOC Search Functionality by Navigating to Search > IOC Searching.
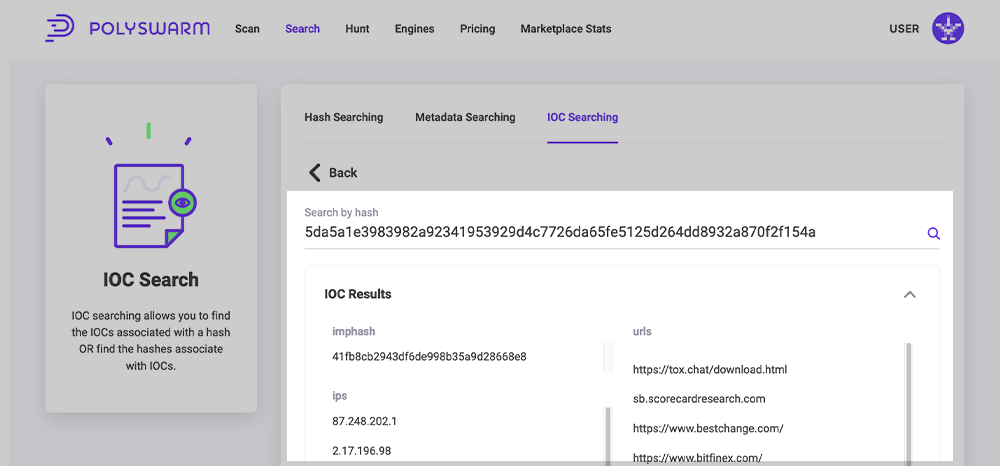
Searching for Associated IOCs
The Default option for this page is the Switch button will be on By Hash meaning searching on a Hash will provide a list of associated IOCs.
Once a hash has been searched, the results page will list the imphash, urls, ips and MITRE TTPs
These associated items have been extracted from the Metadata for the Artifact and have been discovered by Static Tools and Sandboxing.
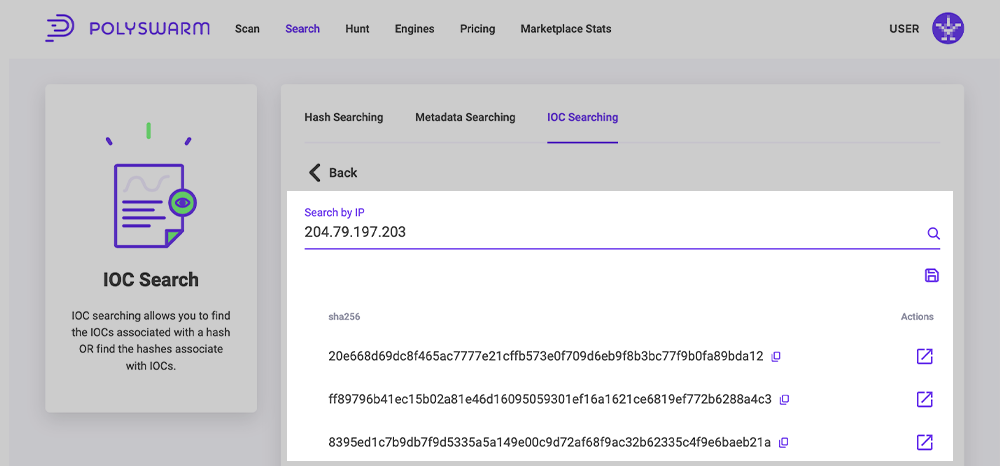
Searching for Associated Hashes
Moving the Switch to the By IOC option will provide the ability to search on a IOC (imphash, urls, ips and MITRE TTPs) and find related hashes.
This page provides the ability to select a start and end date criteria for the hash results to meet, and choose the IOC type.
Once an IOC has been searched on, the results table will show a list of sha256 hashes that are associated to the IOC along with the ability to Download the results as a csv and view each result in a new tab.