Sandbox
On the Sandbox page in the PolySwarm UI, we support Sandboxing Files directly, and managing current submissions.
To use Sandboxing functionality, you must have this paid feature enabled on your Plan, you can check your Usage page to see if you have this.
Submit to Sandbox
The Submit to Sandbox button offers the ability to submit new Artifacts or Artifacts already in PolySwarm to be detonated on the Sandboxes by a chosen Sandbox provider. Sandbox Analysis will take around 2-5 minutes before the results can be accessed.
This is a direct Sandbox submission, meaning the artifact will go directly to the sandbox and not for Scanning by the AV Engines, if you want to Scan a file then you need to upload the file via the Scanning upload. Alternatively, once the file has been Sandboxed you will have the ability to "Rescan" the artifact by the AV Engines.
If you are using the Public Community, the default is that Sandboxed Artifacts will be detonated on the Sandbox with Internet Outreach. If you are using the Private Community, the default is that Sandboxed Artifacts will be detonated on the Sandbox without Internet Outreach.
The Submit to Sandbox button presents a popup with the following options:
- File, Select a local artifact to be uploaded to PolySwarm for Sandboxing
- Hash, Search for a artifact already in PolySwarm by hash value
-
URL, Paste in the URL that you wish to Sandbox
- Choose which Sandbox Provider and detonation VM image to use, currently PolySwarm offers
CapeandTriageproviders with different detonation images for each.
- Choose which Sandbox Provider and detonation VM image to use, currently PolySwarm offers
Provide the artifact or hash, select the Sandbox provider, and select the detonation VM, then click the Submit button to schedule the Sandboxing detonation task. Once submitted, you will return to the My Sandbox page where you can monitor the status of the task.
Sandboxes have multiple returned statuses,
PendingWhen you submit and its queued up ,Delayedin the queue but a delay in processing ,Successfinished processing correctly,Failed with Quota Reimbursementfinished processing but failed, andtimed out with Quota Reimbursementdelayed in the queue for too long, got timed out and then reimbursement.
Supported File Types
The PolySwarm Sandboxes support many file types, these are listed below.
| Type | Extensions | Sandbox Provider |
|---|---|---|
| Executable | .dll |
Triage, Cape |
| Executable | .upx |
Cape |
| Executable | .exe |
Triage, Cape |
| Executable | .msi |
Triage |
| Document | .chm |
Triage, Cape |
| Document | .hta |
Triage, Cape |
| Document | .iqy |
Triage |
| Document | .doc |
Cape |
| Document | .docx |
Cape |
| Document | .xls |
Cape |
| Document | .xlsx |
Cape |
| Document | .ppt |
Cape |
| Document | .pptx |
Cape |
| Document | .pub |
Cape |
| Document | .pub2016 |
Cape |
| Document | .one |
Cape |
| Document | .mht |
Cape |
| Document | .hwp |
Cape |
| Document | .ich |
Cape |
| Document | .inp |
Cape |
| Document | .pdf |
Triage |
| Document | .rtf |
Triage |
| Document | .slk |
Triage |
| Document | .swf |
Triage |
| Document | .html |
Triage, Cape |
| Scripting | .bat |
Triage, Cape |
| Scripting | .ps1 |
Triage, Cape |
| Scripting | .js |
Triage, Cape |
| Scripting | .jse |
Triage, Cape |
| Scripting | .vbe |
Triage, Cape |
| Scripting | .pl |
Triage |
| Scripting | .py |
Cape |
| Scripting | .vbs |
Triage, Cape |
| Scripting | .wsf |
Triage, Cape |
| Android | .apk |
Triage |
| Android | .dex |
Triage |
| Other | .jar |
Triage |
| Other | .lnk |
Triage, Cape |
| Other | .url |
Triage |
| Other | .jnlp |
Triage |
| Other | .reg |
Cape |
| Other | .xslt |
Cape |
| Other | .xps |
Cape |
32MB is the default "max" file submission size, this is a per-account setting, so it is possible for some users/teams to have a higher limit, if you wish to increase this limit please contact [email protected]
.zip file formats are currently not supported by either Sandboxes.
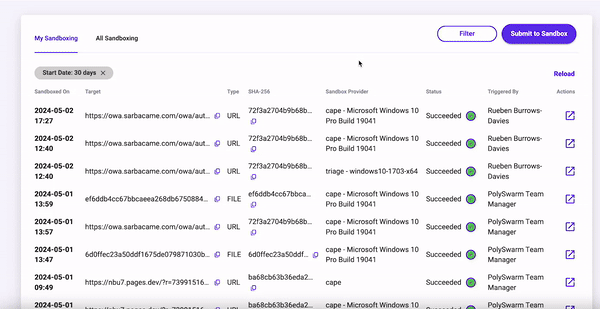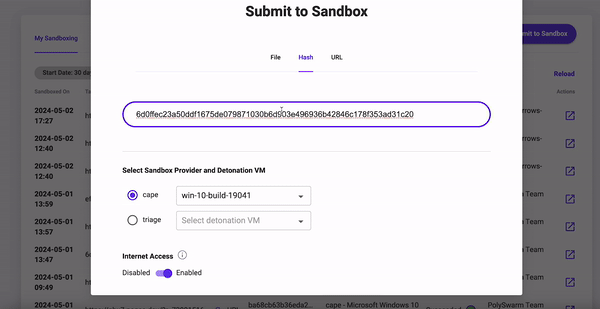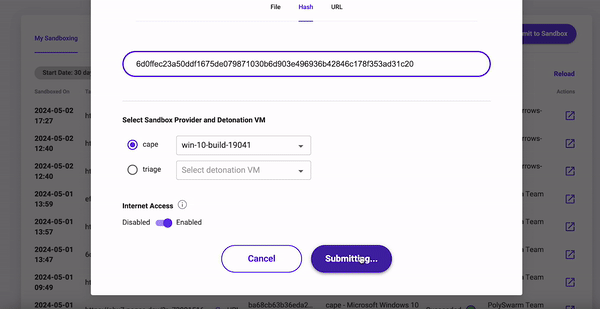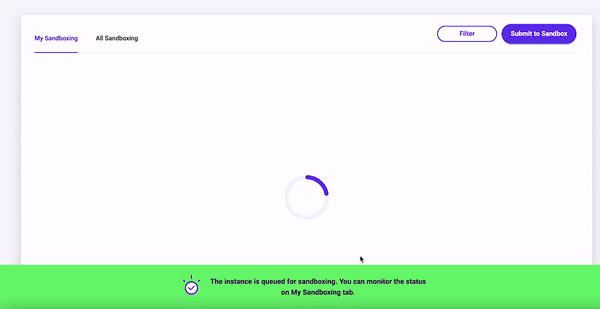
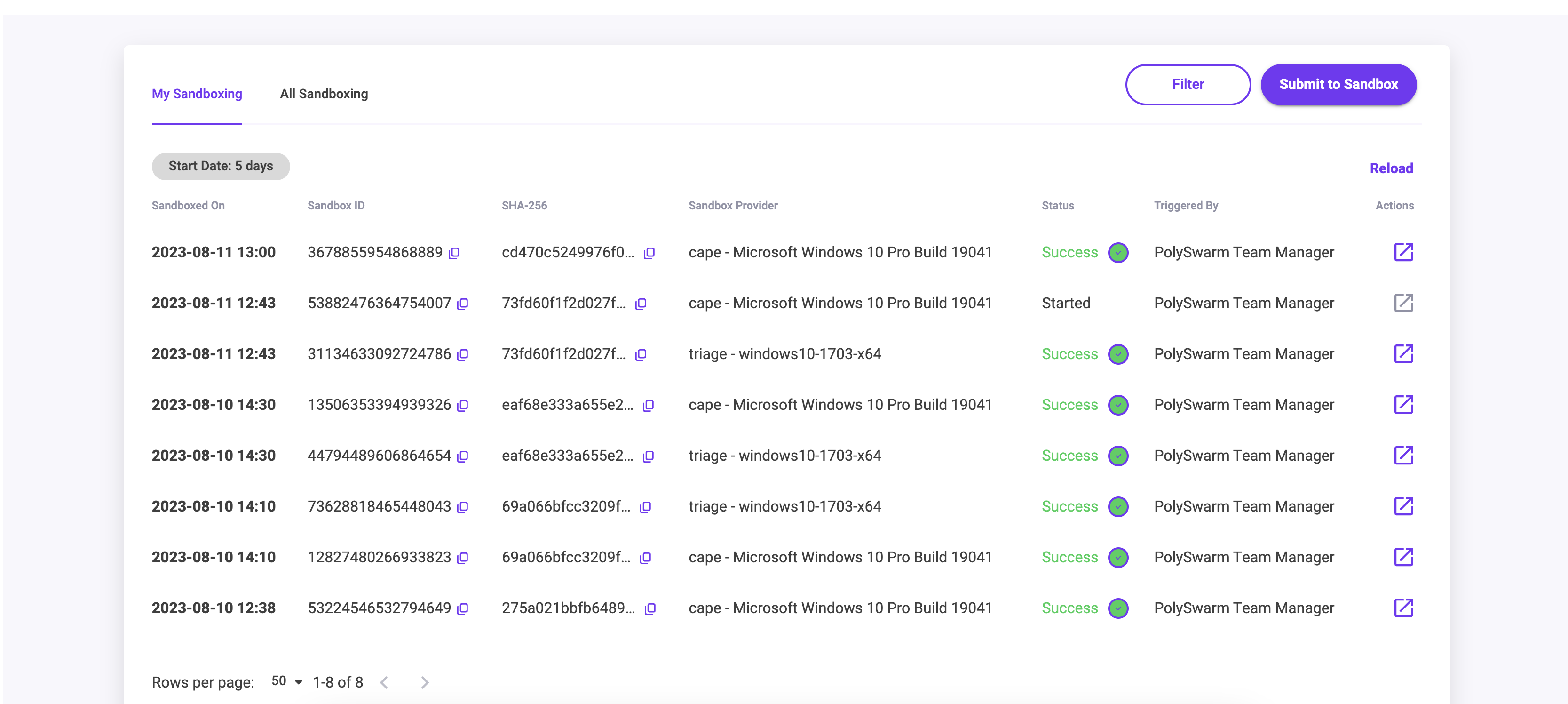
My Sandboxing
The My Sandbox tab shows you Artifacts that you and everyone in your team has Sandboxed, and the status of these submissions.
The table of submissions displays the following information:
| Column | What is it for? |
|---|---|
| Sandboxed On | Date and Time that the Artifact was Sandboxed on. |
| Sandboxed ID | Each Sandboxed Artifact has a Unique Sandboxed ID. |
| SHA-256 | The sha256 of the Artifact that has been Sandboxed. |
| Sandbox Provider | Name of the sandbox provider and the detonation VM used. |
| Status | The status of the Sandbox submission is color coded. The statuses can be: Success, Pending, Started, Timed Out or Failed |
| Triggered By | Name of the PolySwarm User account that triggered the Sandboxing. |
| Actions | Single Action button will open the Sandbox Results Summary page for that Artifact once the Status has changed to Success. |
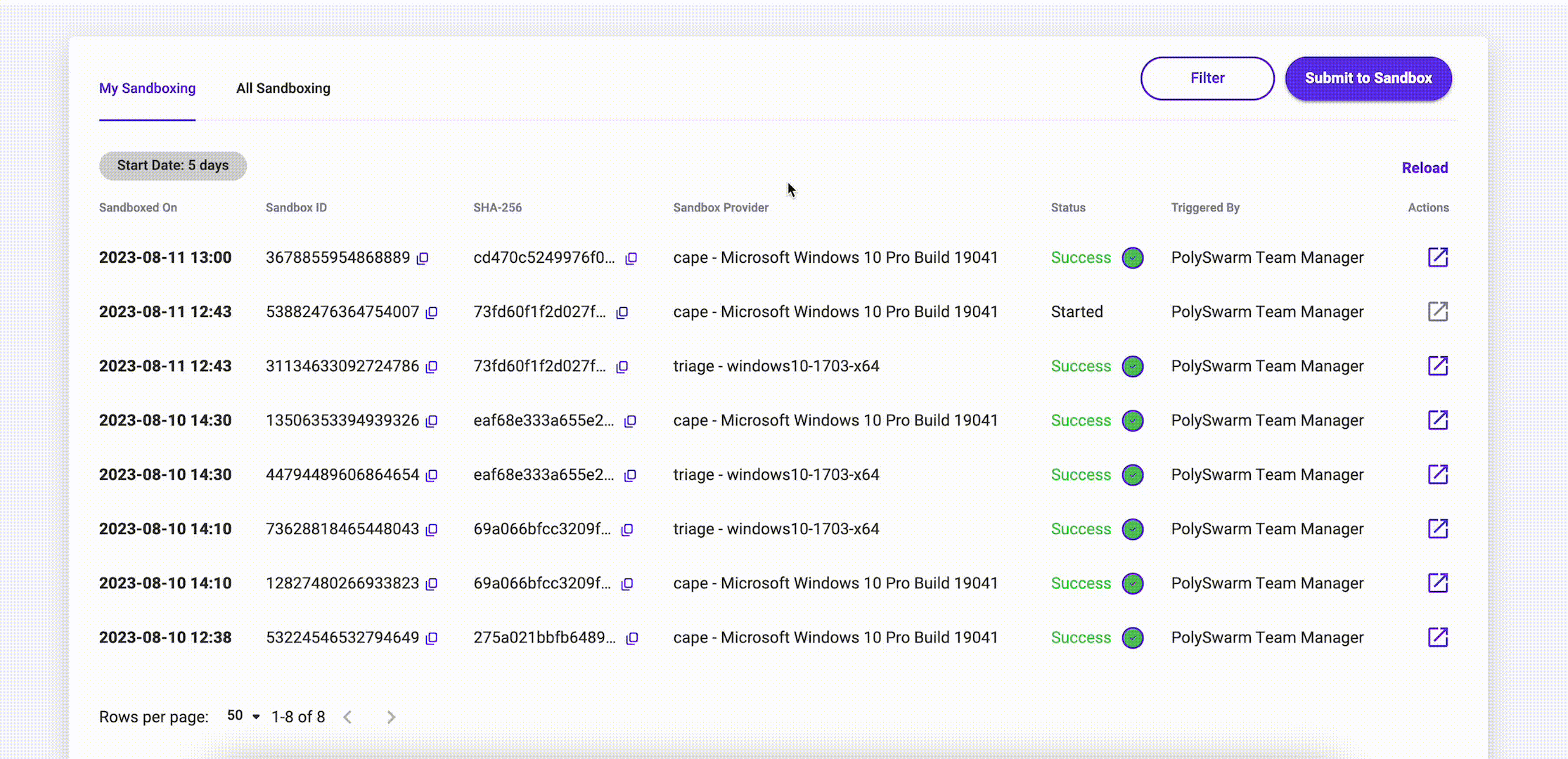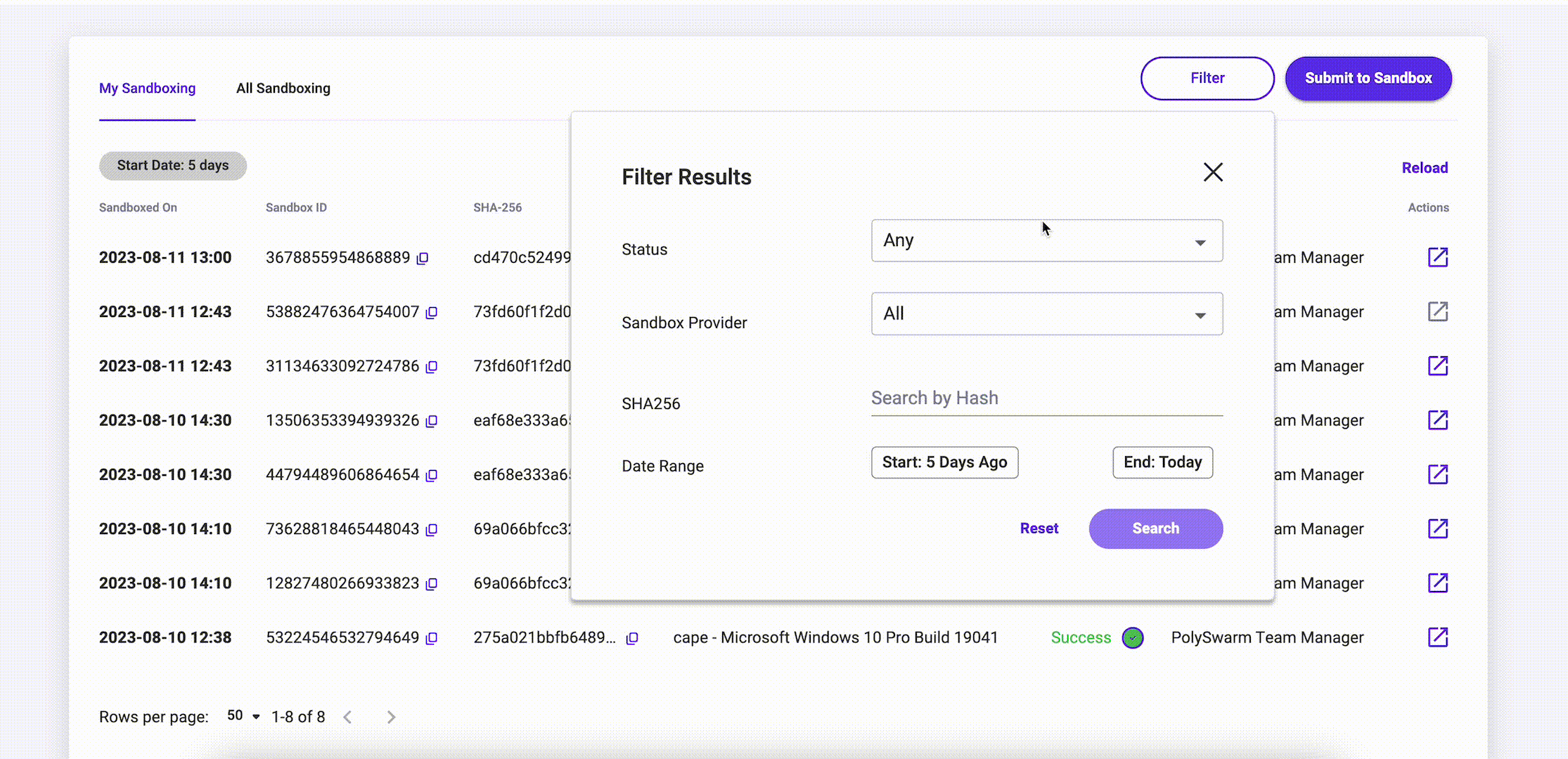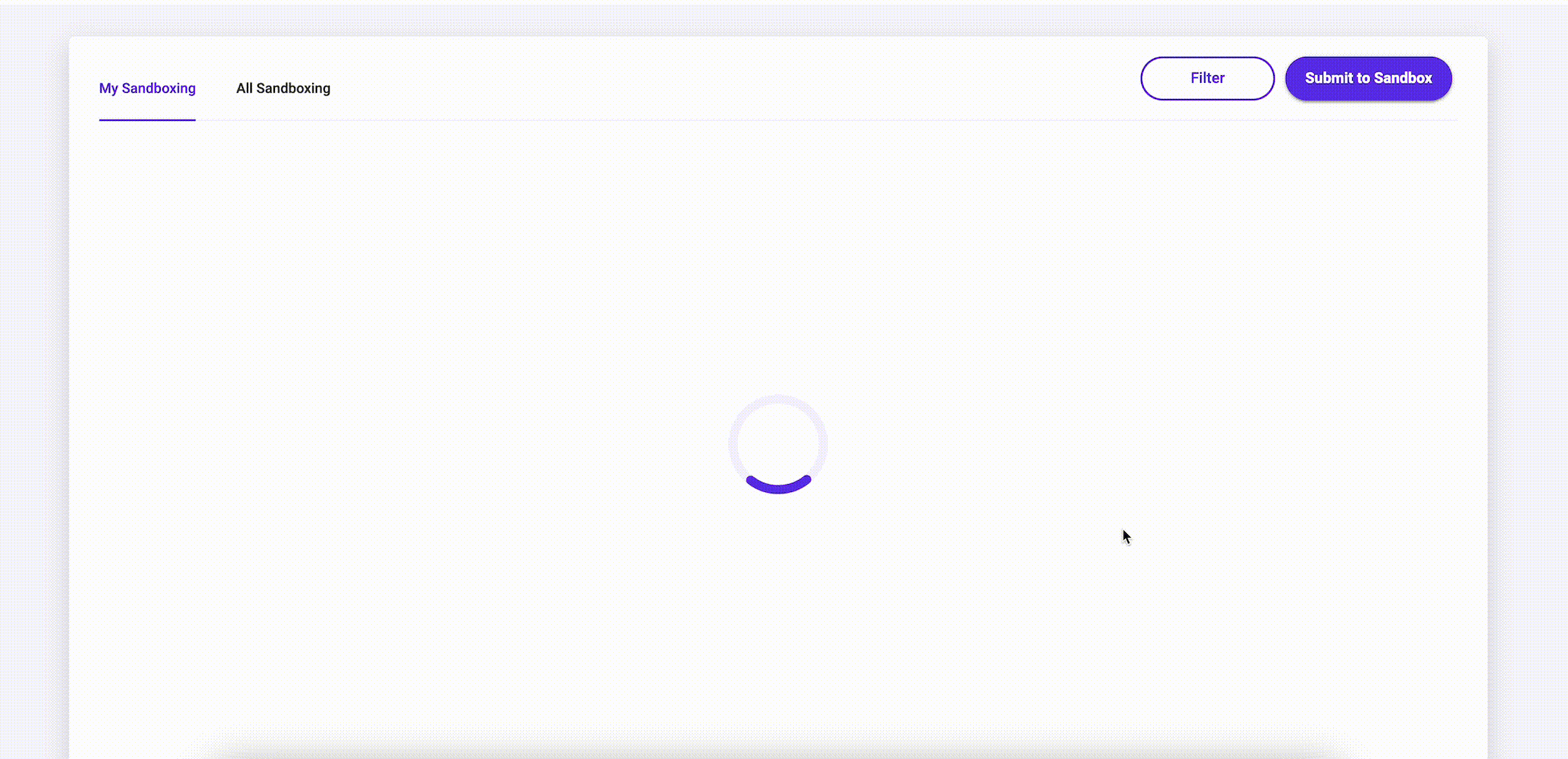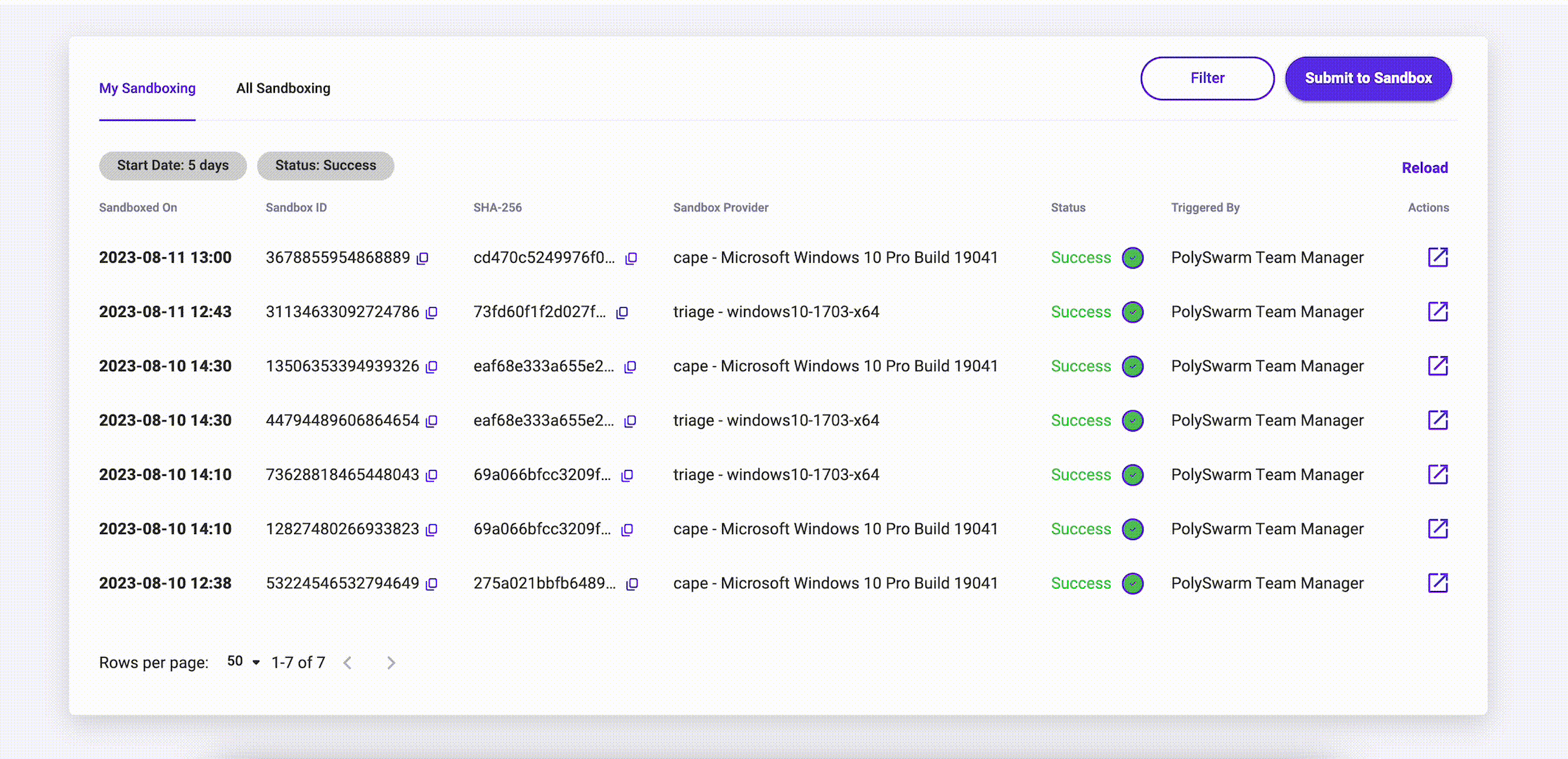
Filtering
The Filter button at the top right of My Sandbox page provides the ability to Filter the results being seen. The following filter options are available:
- Status - Status of the Sandbox submission and can be
Success,Pending,Started,Timed OutorFailed - Sandbox Provider - Name of the Sandbox provider.
- SHA256 - Specific sha256 value of the Sandboxing submission.
- Date Range - Start and End Date for the Sandboxing submission.
At the bottom of the My Sandbox page you can navigate to the next page if further results exist.
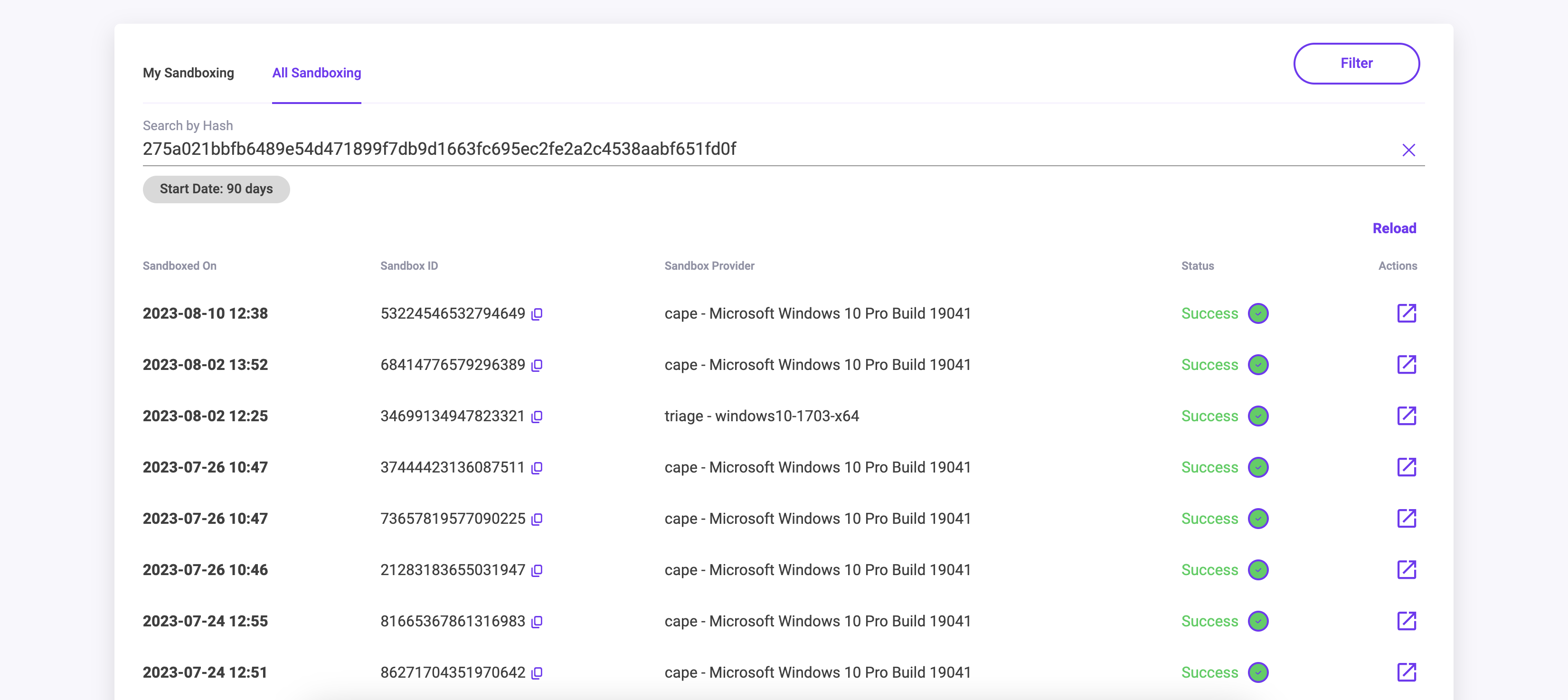
All Sandboxing
The All Sandboxing tab allows you to search by sha256 hash to get a list of every time that artifact was Sandboxed, by any user.
Once you have searched for a Hash value, the table of submissions provides the following information:
| Column | What is it for? |
|---|---|
| Sandboxed On | Date and Time that the Artifact was Sandboxed on. |
| Sandboxed ID | Each Sandboxed Artifact has a Unique Sandboxed ID. |
| Sandbox Provider | Name of the sandbox provider and the detonation VM used. |
| Status | The status of the Sandbox submission is color coded. The statuses can be: Success, Pending, Started, Timed Out or Failed |
| Actions | Single Action button will open the Sandbox Results Summary page for that Artifact once the Status has changed to Success. |
Filtering
The Filter button at the top right of All Sandboxing page provides the ability to Filter the results being seen. The following filter options are available:
- Status - Status of the Sandbox submission and can be
Success,Pending,Started,Timed OutorFailed - Sandbox Provider - Name of the Sandbox provider.
- Date Range - Start and End Date for the Sandboxing submission.
At the bottom of the My Sandbox page you can navigate to the next page if further results exist.
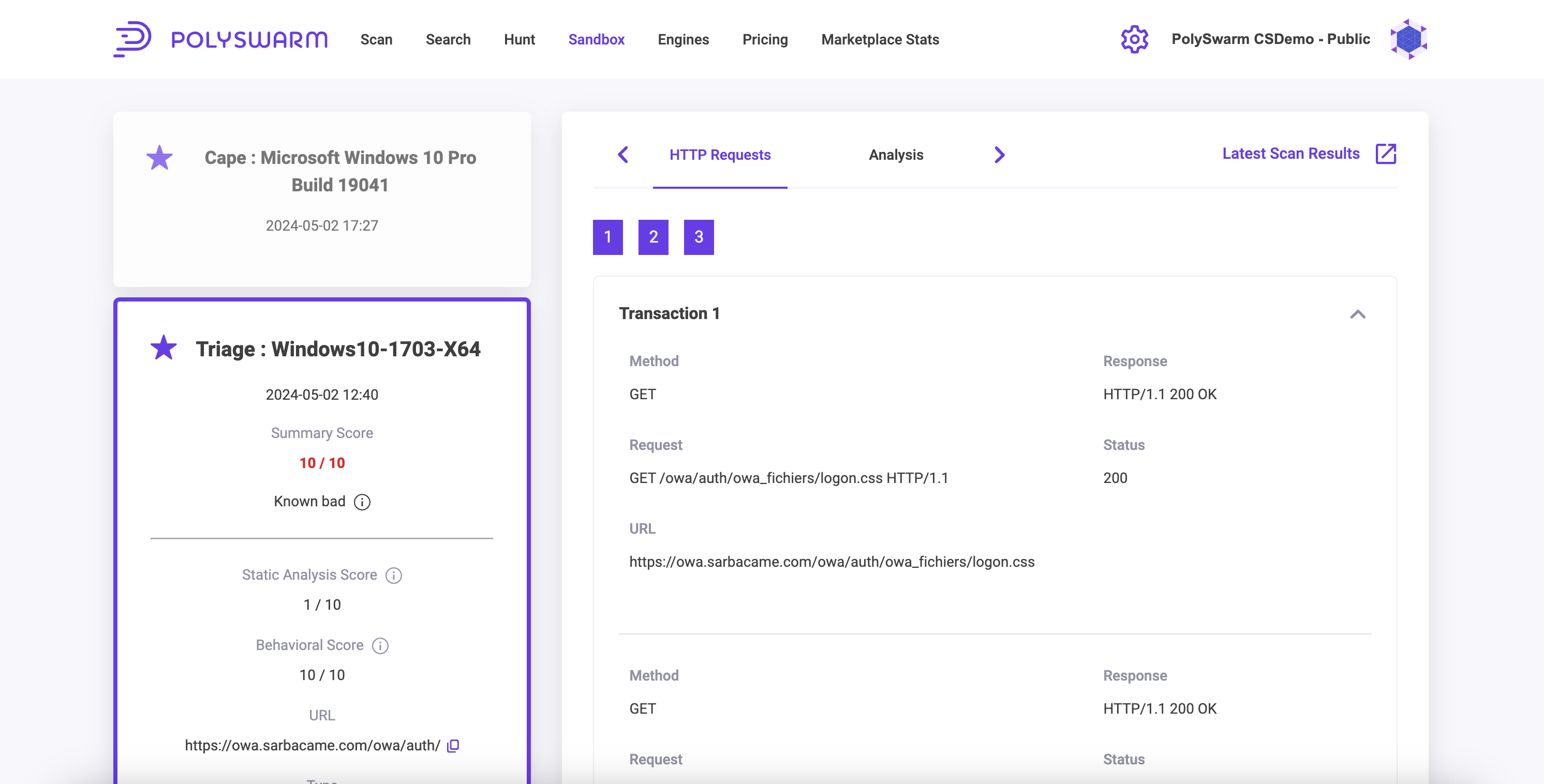
Sandbox Results Summary
This Sandbox Results Summary page provides the view of the latest Sandboxing Results for the Artifact for Cape and Triage.
The page can be accessed from the Action button on the My Sandbox and All Sandboxing pages as well as the Latest Sandbox Results button on the Scan Summary Page for the Artifact.
To view the latest Scan results page for this Artifact you can use the Latest Scan Results button in the top right, then use the Latest Sandbox Results button to navigate back to the Sandboxing detonation results.
Summary Pane
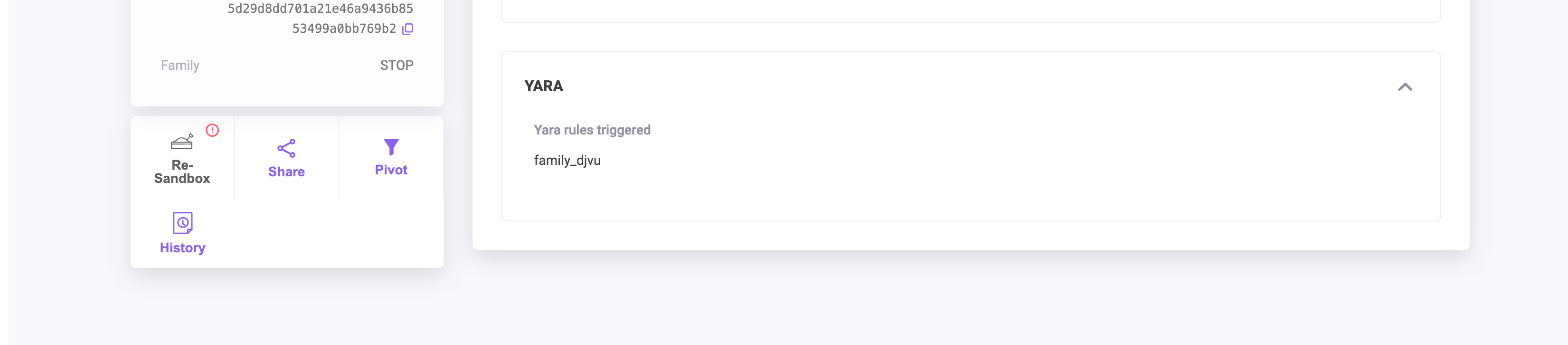
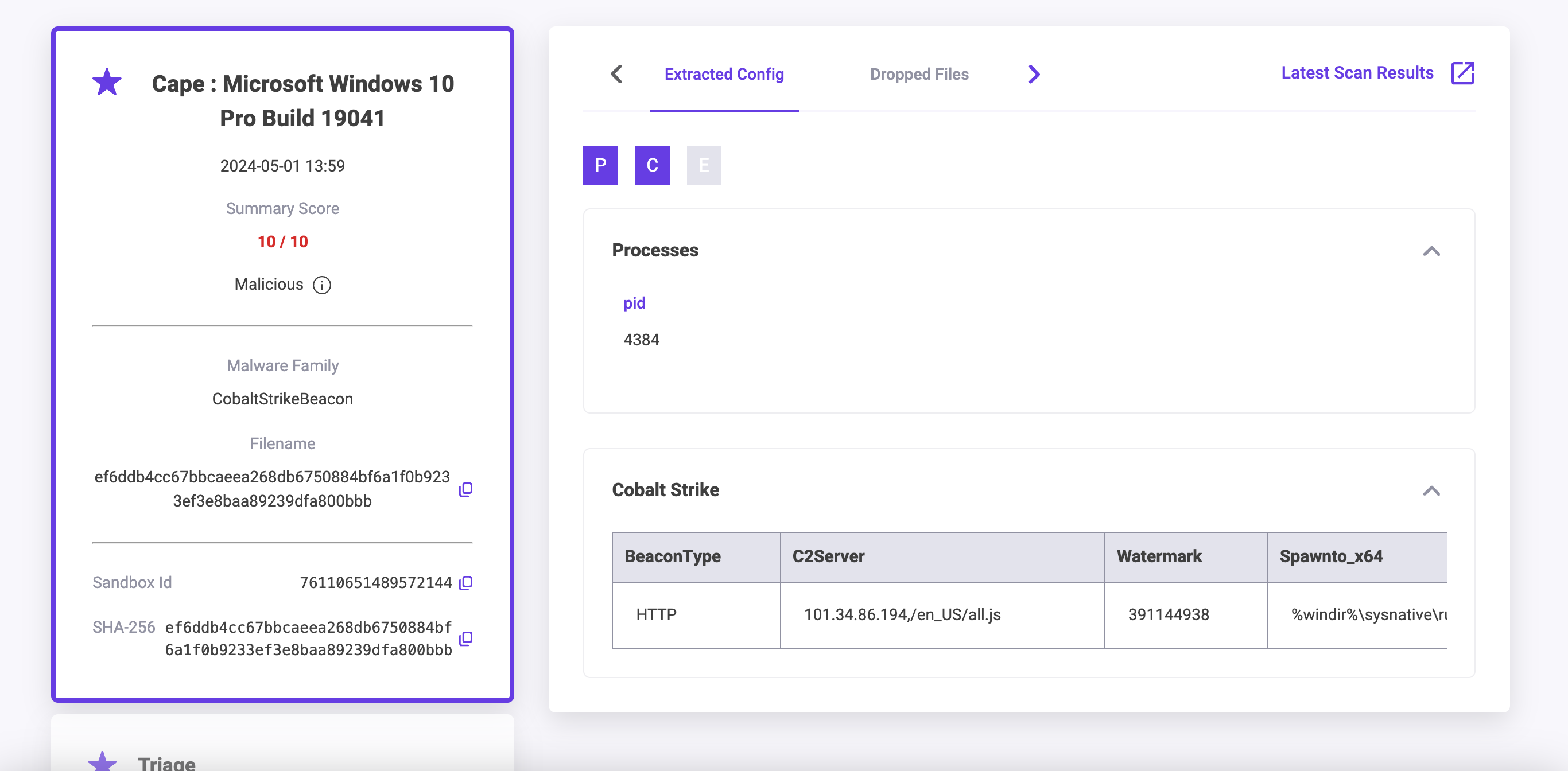
The left Summary pane provides access to either the latest Cape or Triage Sandbox detonation, clicking on either will change the data in the main page body. This section lists the Sandbox ID, sha256, file or url, sandbox score and verdict and the Malware Family.
Below the Summary Pane is the Action Pane with Several buttons:
| Button | What is it for? |
|---|---|
| Re-Sandbox | Re-Submit the Artifact to be Sandboxed. |
| Share | Share a link to these sandbox results page on social media. |
| Pivot | Enable/Disable the pivoting feature. |
| History | See all Sandboxing history, brings you to the All Sandboxing page. |
Sandbox Tabs
The Sandbox Results Summary page has tabs that contain the information from the Sandboxing. This is only a small sample of the data available, to see the fill content download the Full (RAW) JSON for the Sandbox Detonation.
Each Tab has shortcut boxes present, these will be greyed out if the metadata does not exist, click on these to quickly jump to the subsection in the relevant tab.
Extracted Config
This tab contains fields relating to Malware config, Processes and Encryption Keys. Items like Campaign information, Install paths, Access Types and Encryption Key values may be present if the Sandbox has this information. This section can include details from parsers on the sandbox like the CobaltStrike parser.
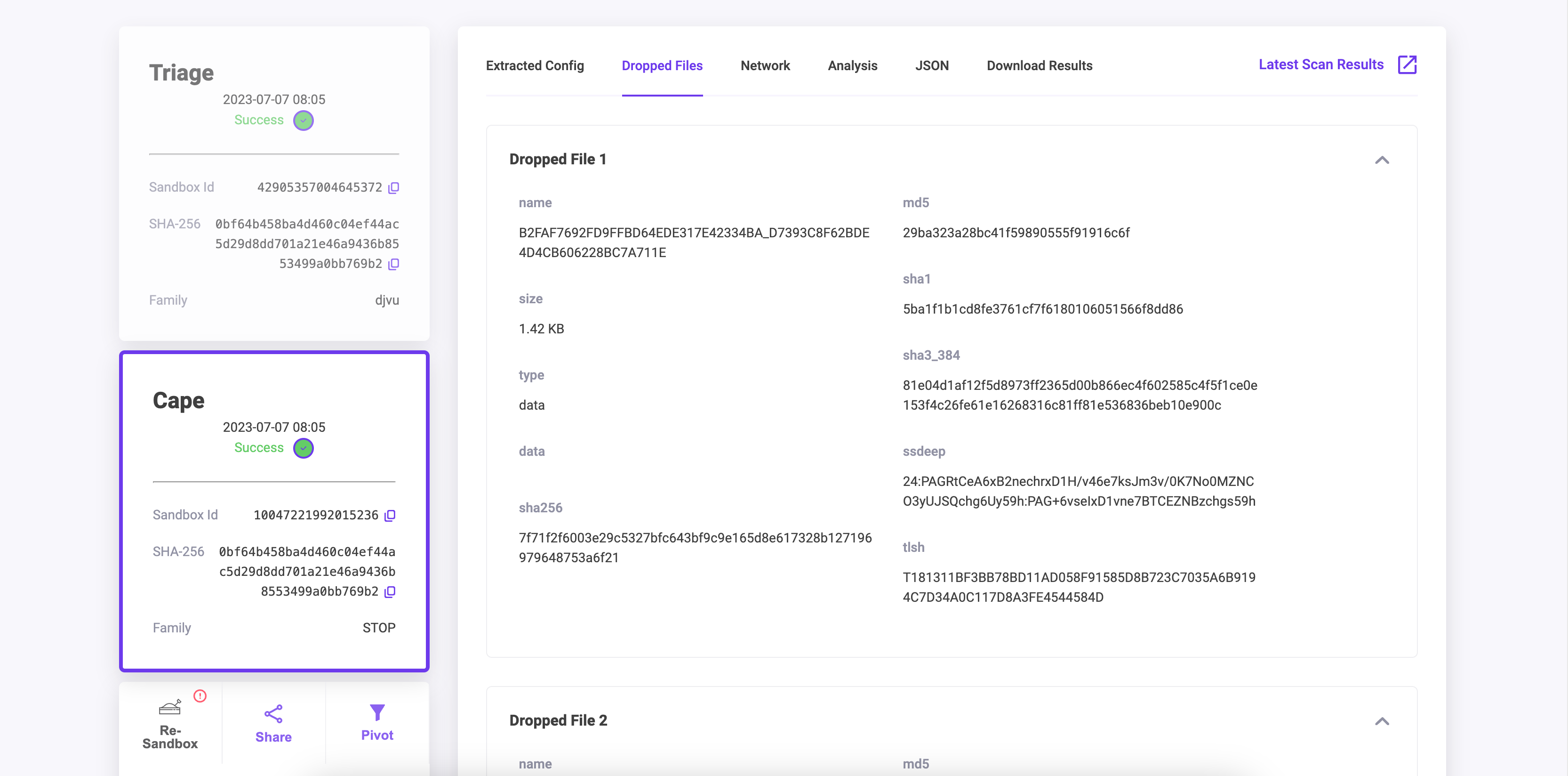
Dropped Files
This tab contains information related to the Dropped Files from the Malware detonation. This tab will display information like File Name, Size, Type and multiple hash values of each dropped file.
Note if you want the dropped file to be detonated in the Sandboxes, perform a Hash Search to lookup that file. On the Hash Search listing, view the Scan results for that file. On that page, you can select the "Sandbox" icon in the Actions Pane to submit it for Sandboxing.
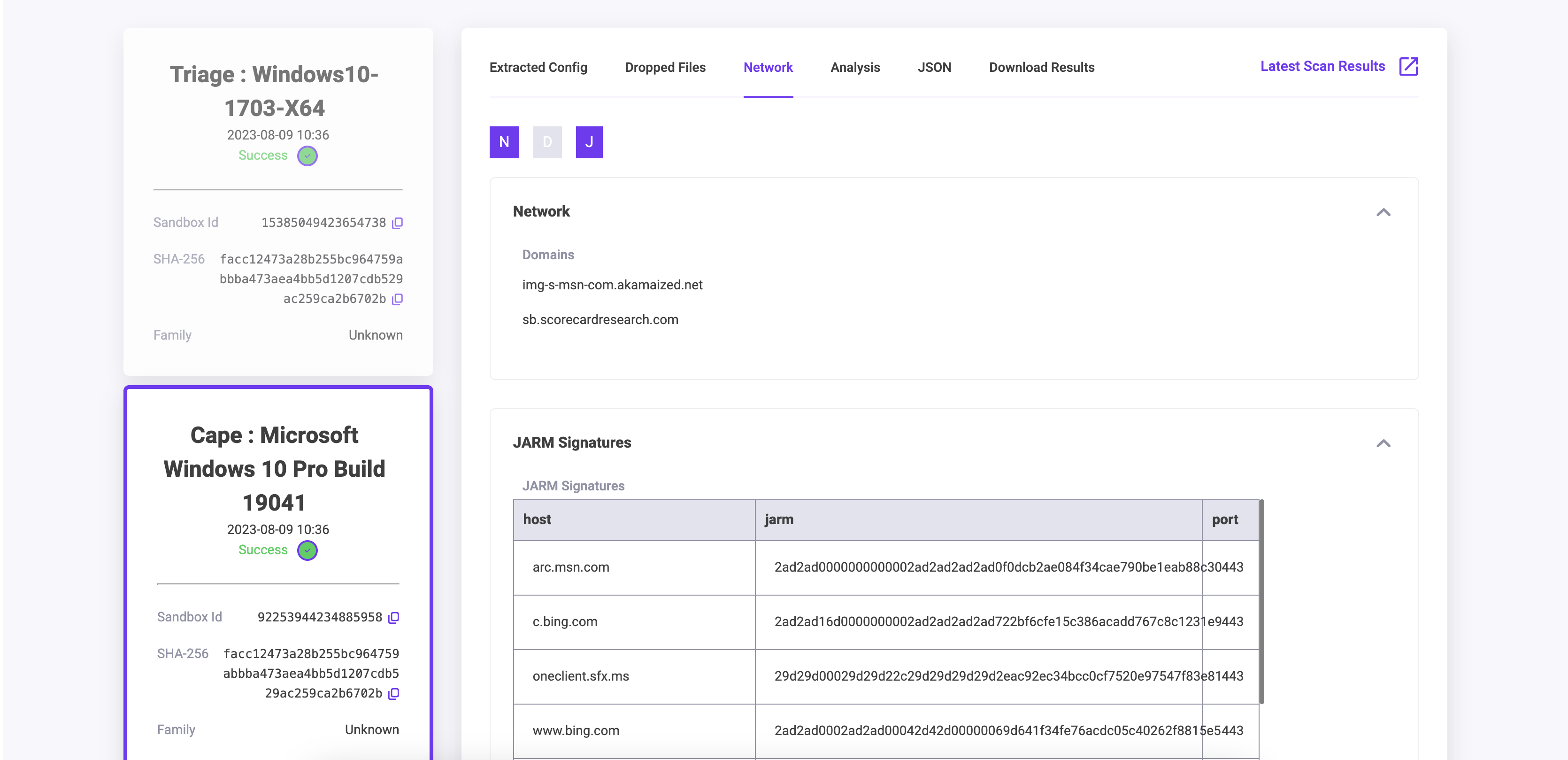
Network Tab
This tab contains information on IPs, SMTP, Domains and JARM details relating to the Sandboxed Artifact. If no data is present then there is no network information available from the Sandbox for this detonation.
HTTP Transaction Tab
This tab contains information HTTP Transactions, this view is only available for Triage Sandboxing sessions.
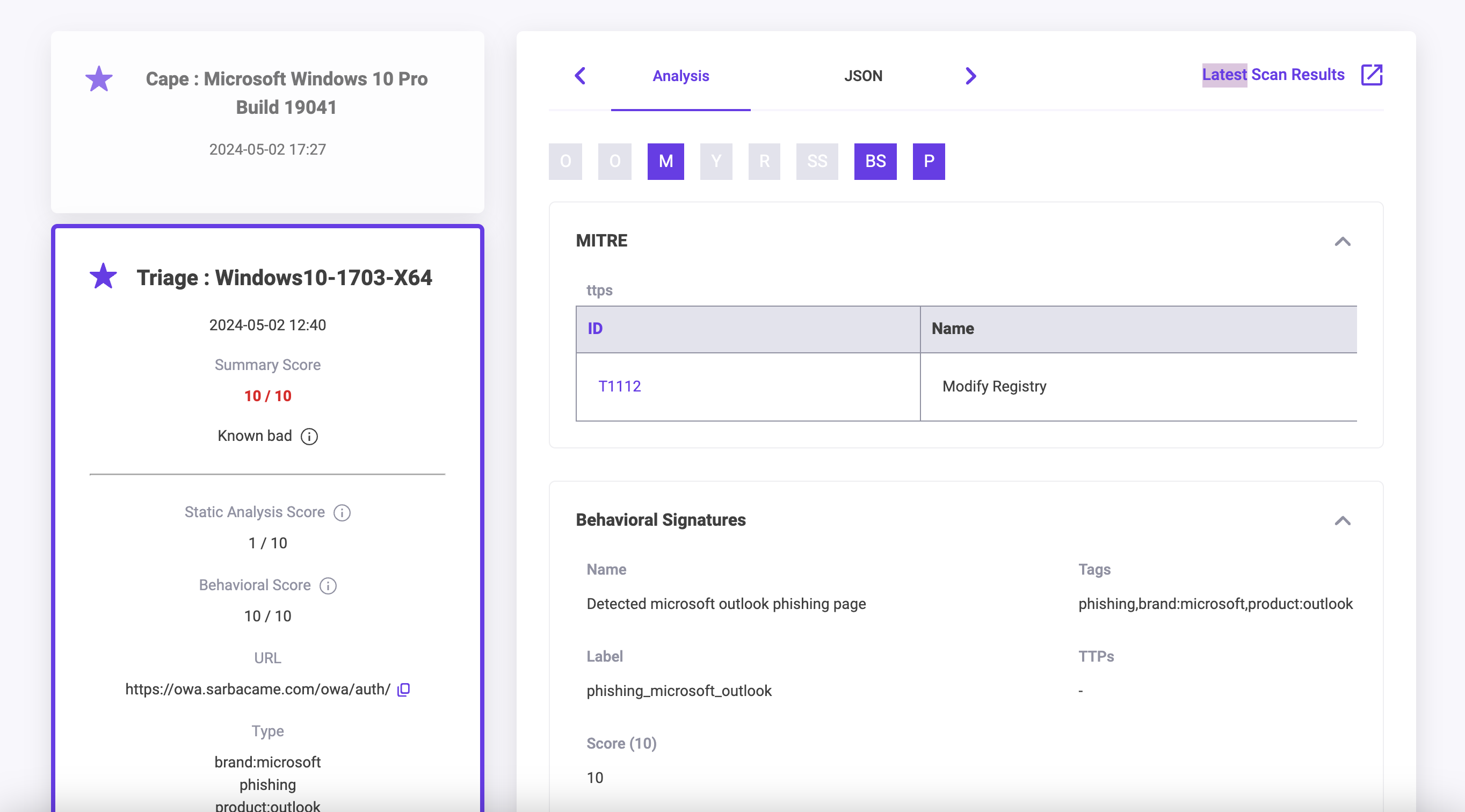
Analysis Tab
This tab contains information on MITRE TTPs used, OS Autorun, Signatures that have been triggered on the Sandbox and Processes. If no data is present then there is no information available for Analysis from the Sandbox for this detonation.
JSON Tab
This tab provides access to the JSON object in relation to the Sandbox detonation, the search field can be used to find specific values and keys. The JSON can be downloaded from this page to be stored locally.
This JSON is the Summary JSON file for the Sandboxing, to download the Full JSON see the
rawreport in the download tab.
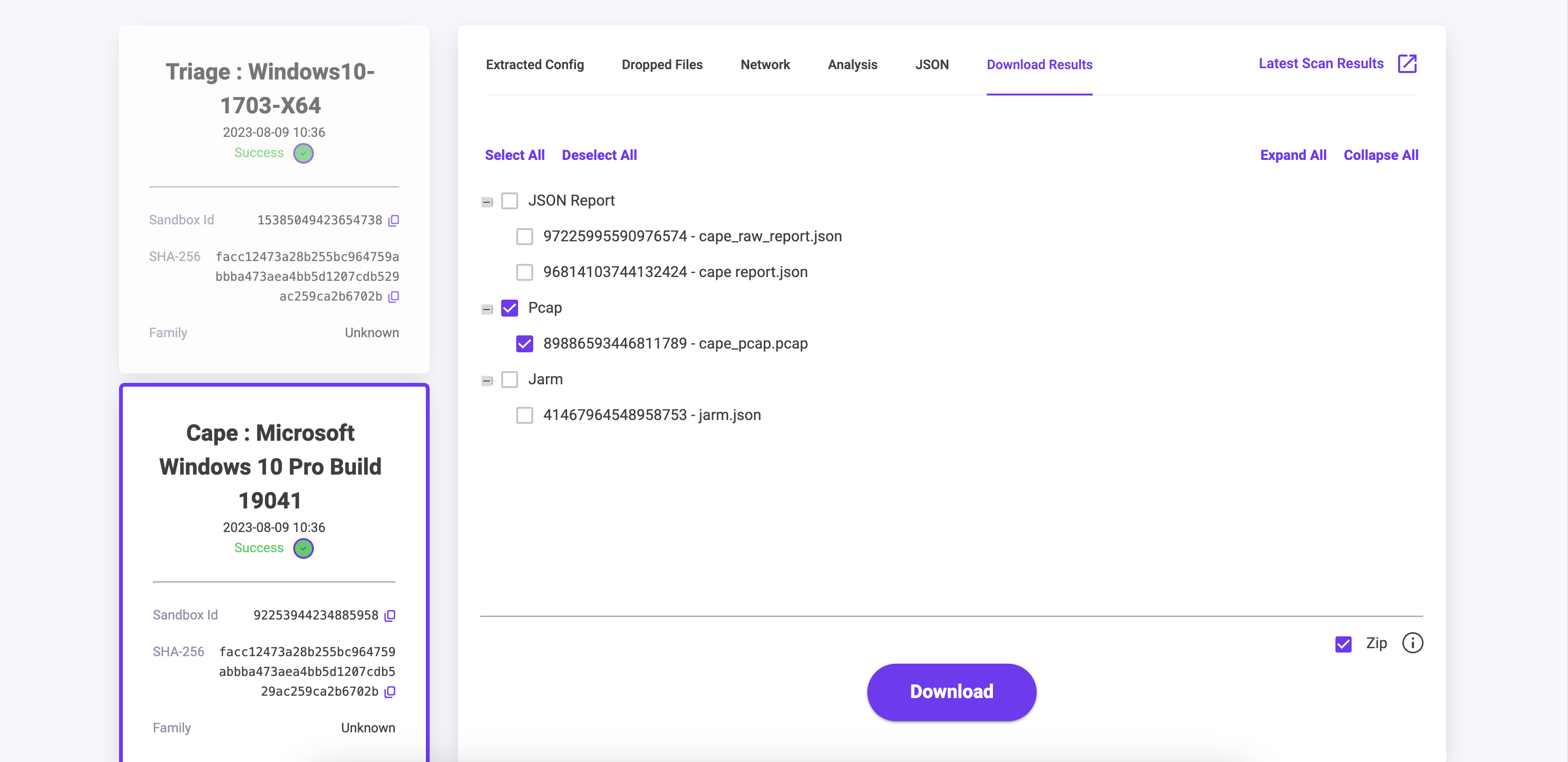
Download Results Tab
This tab allows you to download the Sandbox artifacts. These files can be the JARM file, PCAP Files, full JSON Reports and all dropped artifacts. The dropped files will always be downloaded as an encrypted zip file to prevent trigger your local AV engine.
Each of these files can be downloaded as a single zip by using the zip tick box at the bottom of the page.
The
rawjson is the full report created by the Sandbox, while the regular report is the summarized version used to populate the JSON tab.